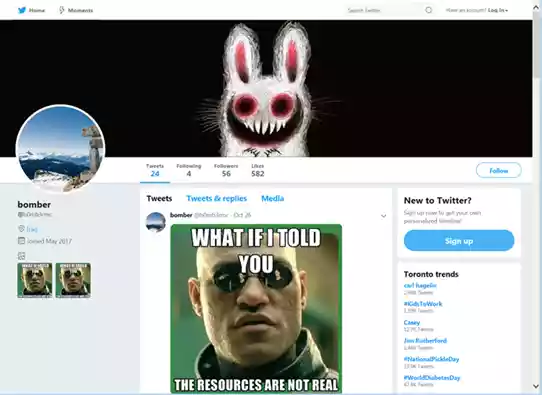
Although the meme looked an ordinary digital image to humans, it had a simple command hidden in the files meta data that was a unique way of it communicating with its creator. The Malware was designed to look up the hacker’s Twitter account and scan images for secret commands. The hacker appears to have only posted two malicious memes on Oct. 25 and 26 with the command “/print,” which will order infected Windows PCs to take a screenshot. Other hidden commands the hacker could’ve sent through the memes include “/clip” to capture clipboard copied content, and “/processos” to retrieve a list of running processes over the PC. Related article:
Major threats: This is how hackers are targeting mobile users. Android’s new feature helps you fight malware
Like most primitive remote access trojans (RATs), the malware quietly infects a vulnerable computer, takes screenshots and pulls other data from the affected system and sends it back to the malware’s command and control server. Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. Hackers use this technique to sneak malicious code into people’s computers or send hidden commands over the web. After Trend Micro reported the account, Twitter pulled the account offline, suspending it permanently as his actions are against Twitters Privacy Policies. Although Twitter didn’t host any malicious content, nor could the tweets result in a malware infection, it’s an interesting way of using the social media site as a clever way of communicating with malware. This is not the first time Twitter has been used by hackers with instances happening in 2009 and 2016.